So in my last post many people are asking what is Spy Note and what can we do by hacking an android. Here is the post regarding it.
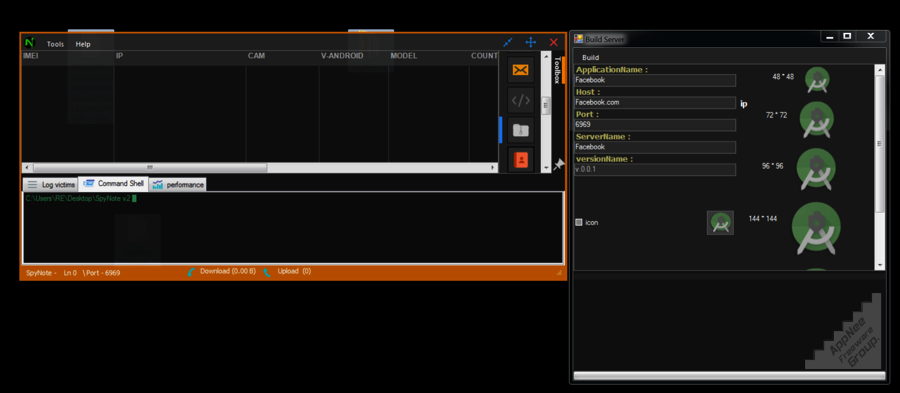
Spy Note is a free Android RAT (Remote Administration Tool/Remote Access Trojan) program developed based on Java. Its Server is written in Java, and the Client controller is written in Visual Basic .NET. After installation on an Android device, Spy Note will automatically remove its on-screen icon from victim’s device.
DISCLAIMER: This website DOES NOT Promote or encourage Any illegal activities , all contents provided by this website is meant for EDUCATIONAL PURPOSE only .
Copyright Disclaimer Under Section 107 of the Copyright Act 1976, allowance is made for "fair use" for purposes such as criticism, comment, news reporting, teaching, scholarship, and research. Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational or personal use tips the balance in favor of fair use.
Spy Note’s essence is a kind of Trojan generator with some quite attractive features. It was popular in the deep web at first, after the leak, it was forwarded around in various malware forums around the world. Installing the Android Trojan app generated by this tool is essentially to transfer your device control power to the hackers (i.e. the maker of this Trojan app) behind the scenes.
As a tool designed for remotely monitoring and controlling Android system/device, Spy Note not only is more powerful than other well-known RAT programs (such as: OmniRAT, DroidJack, Android RAT, Dendroid) in functions, but also comes with more options and better stability (although the connection may be a little unstable sometimes).
As the version upgrades, the features of Spy Note become increasingly powerful, and bring more serious harm to victims. Although Spy Note now seems to have no large-scale use by hackers around the world, today anyone can download it for free means its extensive use may be just a matter of time.
Key Features
- Bind your server APK with any other Game or App
- Install any APK and update server
- Explore Files with full access
- Copy files from device to computer
- Read/Write Messages
- Make a call, record a call and browse call logs
- Read/Write contacts list
- Capture photos and videos via camera
- Listen live conversation through mic, record mic sound live
- Check browser history
- Get GPS Location
- Check installed apps
- Get phone’s information (IMEI, WiFi MAC, PHONE CARRIER)
- Fun Panel (Show messages, shake the phone etc)
- No dependencies, and fully compatible with any Android Version
- No root access required
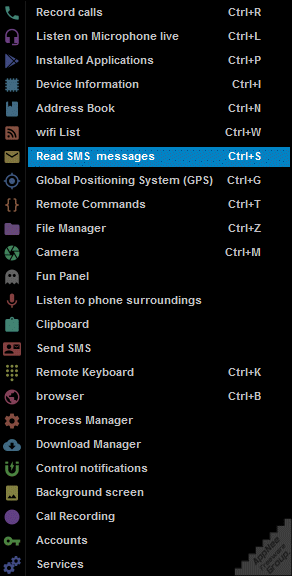
Inbuilt Tools
- Record calls
- Listen on Microphone live
- Installed Applications
- Device Information
- Address Book
- WiFi List
- Read SMS messages
- Global Positioning System (GPS)
- Remote Commands
- File Manager
- Camera
- Fun Panel
- Listen to phone surroundings
- Clipboard
- Send SMS
- Remote Keyboard
- Browser
- Process Manager
- Download Manager
- Control notifications
- Background screen
- Call Recording
- Accounts
- Services
- and more…

Comments
Post a Comment